Endpoint protection in sccm allows you to manage anti malware policies and windows firewall security for client computers in your configuration manager hierarchy.
Heat endpoint security logs.
Choose edit policy and make the changes to the policy.
Client logs can be used for external audit requirements and internal trouble shooting.
Where to find the log files.
Here is table that lists sccm endpoint protection log files and location of each log file.
Log files are generated automatically and stored in the temp folder.
Folders found on disk after you uninstall heat endpoint security client from your pc.
Select the com amazonaws region logs endpoint and choose the policy tab in the lower half of the screen.
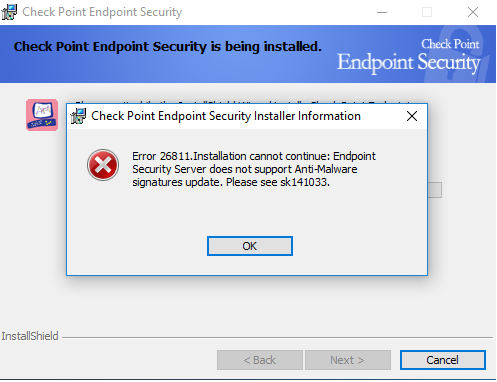
This solution has been verified for the specific scenario described by the combination of product version and symptoms.
Then select com amazonaws region logs and choose create endpoint.
Heat emss 8 4 focuses on the features and usability requirements most requested by our customers said david murray product manager at heat software.
Mcafee endpoint security 10 6 0 common product guide windows log file names and locations.
The suite provides defense in depth endpoint security simplified endpoint management and reduced endpoint total cost of ownership while offering added protection against targeted attacks.
C program files heat software endpoint security client.
The current web page applies to heat endpoint security client version 5 0 168 only.
It may not work in other scenarios.
The following sections list log files that are on the site server or that are related to specific site system roles.
C documents and settings all users application data checkpoint endpoint security logs uploaded according to the common client policy to the endpoint security management server and viewable in the logs tab of the smartconsole logs monitor view.
The log file sms dm log on the site system server also records communication between mac computers and the management point that is set up for mobile devices and mac computers.
Some files and registry entries are usually left behind when you remove heat endpoint security client.